Last Update: 2024 - 05 - 21

Warnings and Trust – Trust Center Settings in Microsoft Office
by Philipp Stiefel, originally published 2024-03-15
last revision on 2024-03-17

Photo by Nick Fewings on Unsplash
If you are working a lot with Microsoft Access database files, like I do, you probably clicked on the “Enable Content” button millions of times, like me. – Only a very slight exaggeration.
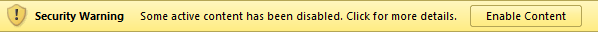
I strongly hope you also think about the risk involved with that simple click each and every time. – Whenever I don’t exactly know what will happen once I click that button or I don’t absolutely trust the source of that file, I will not click that button. Period.
Unfortunately, many users of Microsoft Office applications are not as cautious as we are. They click that button more often and more recklessly than they should. Microsoft, acknowledging this fact, made a change to when this button appears in 2022, and now you might also see this warning without the button.

So, let’s talk about that button, its effects, why it has gone missing for some files, and, most importantly, its alternatives.
The information in this text applies to all Microsoft Office applications from Office 2007 onward, except when explicitly stated otherwise.
It is especially important for Microsoft Access because all Microsoft Access file types may contain Macros and/or* VBA code. Other Microsoft Office applications use dedicated file extensions for files containing Macros/VBA; e.g., .xslm and .docm, hence you will see this warning less often, because it is only relevant for these types files.
Some tabs in the Office Trust Center are only available in some Office applications but not in others. If any of the tabs is available, it will have the same functionality as in every other application where it is available.
*= The terms “Macro” and “VBA Code” are synonyms in all Office applications except Access where these two terms mean different things. The Trust Center dialogs are the same in all Office applications and only mention the term “Macro”, but they mean VBA code, even in Access.
Macro Settings
The options here should be straightforward and I’m not going to explain them in detail. However, one fact is much less straightforward: These settings apply only to files that are neither a Trusted Document nor in a Trusted Location. If you choose to “Disable all macros without notification”, macros (VBA code) in these files will still be executed.
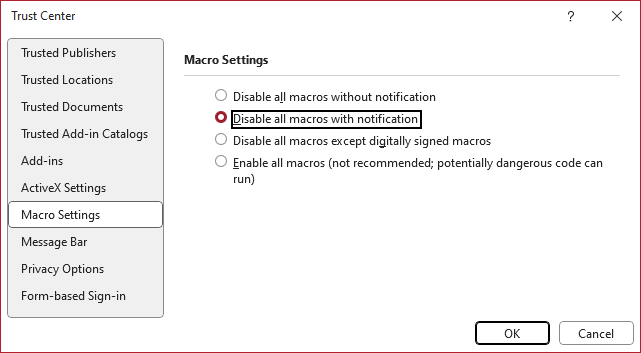
You will see the warnings I talk about and the somewhat risky “Enable Content” button only, if your Macro Settings in the Trust Center are set to “Disable all macros with notification” – This is the default, and basically the option that makes the most sense if you sometimes do want to run macros and/or VBA and are not using Trusted Locations or digitally signed files exclusively.
Message Bar
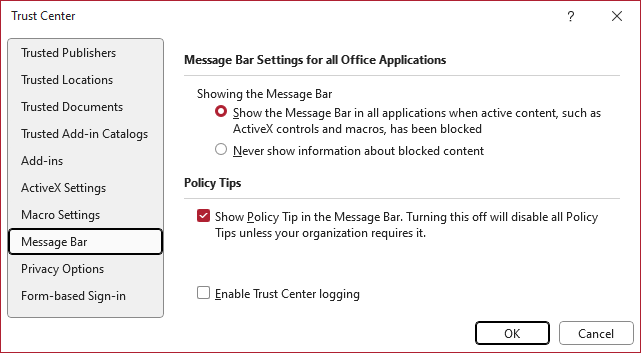
“Showing the Message Bar” is only about the display of the bar containing the warning text and the corresponding button. It only hides the information but does not change the behavior of the Office app beyond that. The “Enable Content” button is no longer visible right away when opening a document, but the functionality is still available if you go to “File” – “Info”.
Trusted Documents in Microsoft Office
When you click the “Enable Content” button, you make the current file a Trusted Document, probably without being aware of this fact.
Only if you click the link “Some active content has been disabled. Click for more details.” you will be explicitly informed about this fact and get the option to choose to enable the content for “this session” only, which means until you close the document.
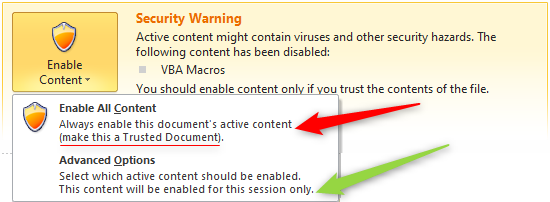
If you (or your network administrator) disabled Trusted Documents, the “Enable Content” button will also just enable the active content for the current session. – However, this is not obvious at first glance.
Using the default behavior of “Enable Content” to make the current file a Trusted Document is not ideal for 3 reasons.
1. Maintenance Nightmare
It is very difficult to keep track of Trusted Documents. There is no list of those documents displayed anywhere in the UI. Thus, it is also very difficult to “untrust” a document. The full file name of each Trusted Document is stored in the Windows Registry. Viewing and editing the Registry manually is the only way to manage Trusted Documents beyond just clearing all of those at once.
The individual Trusted Documents are stored in this Registry path:
With Version being the version of your Microsoft Office installation, e.g. 16.0, and AppName being the name of the relevant Office application, e.g., Access.
2. Potential Security Risk
Trusted Documents are primarily identified by their full file path. If you ever downloaded a database file provided by a trusted colleague, which was very creatively named “Test”, “Demo” or “Database1”, made it a trusted document right in the Downloads folder, and then deleted it again, …
… any new file with the same name in this folder, even when downloaded from an entirely different source, will also be a Trusted Document!
It’s not just that simple. There are additional factors involved and I don’t understand all of those completely. Nonetheless, I was able to craft a custom pair of documents with one being “harmless”, while the other is “malicious” (simulated only!) and able to assume the identity of the harmless document, after that was made a Trusted Document. – The verification of the MotW (see below) mitigates this risk in newer versions of Microsoft Office.
3. Poor Performance
In current versions of Office 365 (as of 2024-02-29), VBA code in a Trusted Document may run more than 20 (twenty!) times slower than it would in a different scenario. The reason for this is that before each line of code is actually executed, it is passed on to the Antimalware Scan Interface (AMSI) and checked for indicators of malicious behavior. This code verification is not just performed once, but always and continuously when code in such a document is executed.
This type of scan must happen at runtime, while the code is executed, because if malicious code got this far, it must already have bypassed static malware scanning by obfuscation, encryption, or similar means.
In case your installed anti-malware software indicates that the code is actually malicious, AMSI will terminate your Office application to prevent further execution of the code.
I didn’t find out about this performance issue myself. All credit belongs to Aleksander Wojtasz who first discovered the issue and Colin Riddington (aka Isladogs) who published these findings.
Blocked Files – Mark of the Web (MotW)
In the introduction of this text, I mentioned that you might also see a warning “Microsoft has blocked macros from running because the source of this file is untrusted.” without a button to enable the content.

This was done by Microsoft in 2022 to prevent users from clicking recklessly on the “Enable Content” button, even though there is an increased risk of the file being not trustworthy.
The untrusted source referred to in the message is usually the internet. Most current web browsers will add the Mark of the Web (MotW) to each file you download to an NTFS file system folder. The MotW is an alternative data stream of the file, which contains zone identifier data. – The MotW is not really new. It was introduced with Windows XP already. New is that now Microsoft Office uses this information to assess the security risk of a certain file.
You can use the Get-Content PowerShell cmdlet with a -stream argument of Zone.Identifier to view this alternative data stream.
Here is an example of a file downloaded from this website:
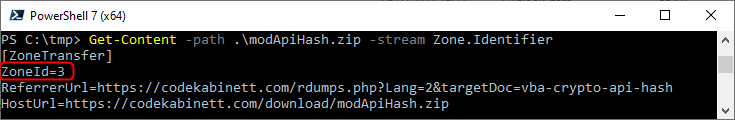
The most important information is the ZoneId, which refers to an URL Security Zone. A value of 3 indicates the file was downloaded from the internet. This is the essence of the MotW. The other attributes in the Zone.Identifier are optional and may vary depending on the application which you used to download the file.
The Zone.Identifier stream will be stored with each file until you either copy the file to a file system, which does not support alternative data streams, or you explicitly remove it.
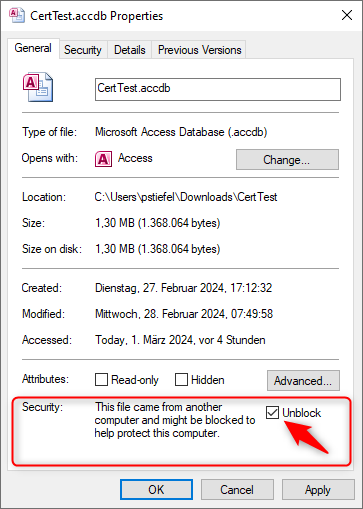
The MotW can be easily removed by viewing the file’s properties in Windows Explorer, checking the Unblock check box and applying the change. Once you do this, you will see the “normal” warning again if you open the file in a Microsoft Office application.
If you move a file to a Trusted Location, the MotW has no more effect on the execution of Macros/VBA in an Office application, but it is still present in the file.
Trusted Locations in Microsoft Office
You would think Trusted Documents and Trusted Locations operate the same way, share the same advantages, disadvantages, and risks, except one is for individual files and the other for whole directories. – Luckily, this is not the case.
In general, Trusted Locations are the recommended approach to explicitly allow Macro/VBA code execution for files you trust. To understand why this is the case, let’s compare the functionality of Trusted Locations to the issues mentioned above:
1. No Maintenance Issue
Trusted Locations must be manually configured in the corresponding Trust Center dialog.
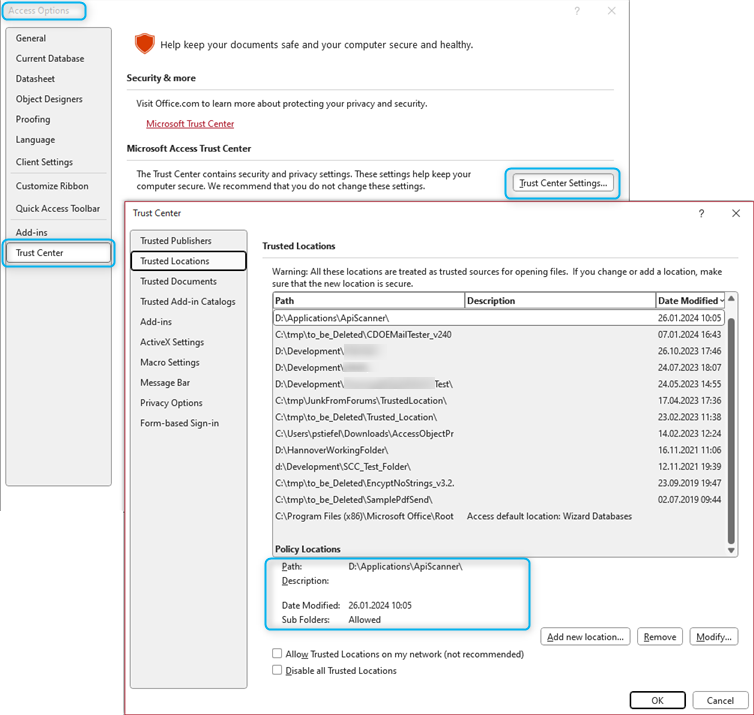
This is a clear, sortable list of the existing locations, including their last modified date, whether they include subfolders, and optionally even a description of their purpose in the details section below the list. You can also modify or delete them easily.
Trusted Locations are also stored in the Windows Registry. Again, they are configurated separately for each Office application and version.
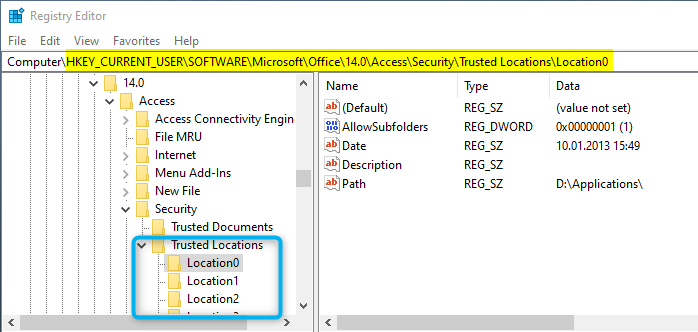
If you are using the Microsoft Access Runtime, the functionality of the Trusted Locations is the same. – However, the Trust Center dialogs to view, and edit are not available. So, you then need to either edit the Registry manually or use a script to add/edit/remove a Trusted Location.
There may also be similar entries in the HKEY_LOCAL_MACHINE branch of the Registry if your administrator has preconfigured Trusted Locations for all users on the computer. If the computer is part of an Active Directory domain and maintained by a competent administrator, they can also configure Trusted Locations by using a Group Policy.
2. Much Lower Security Risk
Usually, you must create a new Trusted Location for a file containing VBA code or move it explicitly to an existing one. The risk of users skipping due process and doing this accidentally is quite low.
Of course, you can make your Downloads folder a Trusted Location and thus create an even bigger risk than with a downloaded Trusted Document. However, it should be obvious that this is a high-risk decision. – If you point an unlocked and loaded gun to your foot, you create an unnecessary risk to shoot yourself.
The general rule is to never make a folder a Trusted Location if it is likely that documents end up there without your explicit intent. Your own Documents folder, any temporary folder, or any folder accessible on the network are poor choices for a Trusted Location.
3. No Performance Penalty
Trusted Locations do not suffer from the performance penalty of AMSI scanning. This is not explicitly stated in the above linked documentation of AMSI, but Microsoft makes it quite clear in this text about effects of the AMSI malware runtime scan.
Trusted Publishers / Digital Signatures
There is an alternative to Trusted Locations, which is equally, if not more, useful in its effects, but significantly more complex to implement.
You can digitally sign your Access applications with a code signing certificate. Then users of your applications just need to trust you (rather your certificate) once and all your signed applications will enjoy the same trust as if they were in a Trusted Location even if they aren’t. – This only applies to documents signed by you, which were not modified after you signed them.
This topic is beyond the scope of this article. I will publish another text dedicated to signing Access and VBA applications very soon.
Conclusion
Most Office users do certainly not need to know all these details. However, if you professionally develop Access and VBA applications, you should be aware of these to appropriately advise your clients.
There are surprisingly many aspects to this seemingly simple topic. I myself learned a lot by researching and writing this text.
I will never share your email with anyone. You can unsubscribe any time.
This email list is hosted at Mailchimp in the United States. See our privacy policy for further details.
© 1999 - 2024 by Philipp Stiefel - Privacy Policiy



